
What is 3G and how will the 3G Sunset affect your Security System?
In order to explain what the 3G Sunset is, it’s important to understand the evolution of mobile broadband.
It’s hard to believe there was a time when we didn’t have smartphones or instant access to information. The evolution…
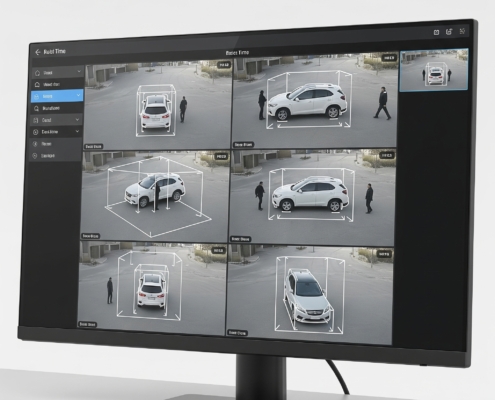
The Evolution of Video Analytics Beyond Basic Surveillance
For years, commercial security largely relied on a simple premise: cameras capture footage, and someone watches it. While this "basic surveillance" offers a vital deterrent and retrospective evidence, it's akin to having a library full of books…

Level Up Your Security – How 5G is Revolutionizing Commercial Systems
Security is no longer a static measure; it's a dynamic and evolving necessity. At HS Tech Group, we understand that staying ahead of potential threats requires embracing cutting-edge technology. That's why we're excited about the transformative…

A Guide To Choosing the Right Commercial Alarm System
Protecting your commercial property is paramount. A reliable alarm system can deter intruders, alert authorities in case of a break-in, and potentially reduce insurance premiums. But with so many options available, how do you choose the right…

The Comprehensive Benefits of Digital Signage for Business
In today's competitive market, businesses constantly seek innovative ways to improve communication and engagement with their patrons. Digital signage has emerged as a powerful tool to achieve these goals, offering a dynamic platform for advertising,…

Benefits of Remote Guard Services for Remote Locations with Automatic Gates
Remote locations often pose unique security challenges, especially when they require after-hours access without an on-site attendant. Remote guard services have revolutionized the way these sites are monitored and managed, providing efficient,…

Why Choose a Boutique Central Monitoring Station: 10 Reasons It Might Be the Better Choice for Your Home or Business
In the realm of security, selecting the right central monitoring station is paramount. While larger national stations offer extensive resources, boutique monitoring stations provide unique advantages that can be more suitable for some homes…

Advances in Video Surveillance for Remote Locations: Solar Power and Cellular Communication
In recent years, advances in technology have revolutionized video surveillance, making it feasible to monitor remote locations that lack access to traditional power sources and internet connectivity. The combination of solar power and cellular…

Top 10 Advances in Electronic Security to Delay and Deter Potential Active Shooters
In an era where school safety is a paramount concern, the integration of advanced electronic security measures has become crucial in safeguarding students, teachers, and staff. These technologies not only help delay or deter potential active…

Ionization vs. Photoelectric Smoke Detectors
Smoke detectors are essential devices for ensuring the safety of your home and loved ones. They provide early warning in the event of a fire, allowing occupants to evacuate quickly and potentially save lives. However, with different types of…

Unveiling the Top 5 Benefits of Alarm.com’s New Exterior Drone Partnership with Sunflower Labs
Last week at ISC West, the world's leading security industry event, Alarm.com made waves with the announcement of an exciting new partnership with Sunflower Labs, unveiling their groundbreaking Exterior Drone. This collaboration between two…

How Security Foggers Secure Your World
In the realm of security technology, there exists a powerful guardian that operates beyond the conventional realm of alarms and surveillance cameras. It's a revolutionary tool known as a security fogger, and it's transforming the landscape of…

Understanding the Four Levels of Safe Haven Safety Glass for Homes and Businesses
In the realm of home and business safety, the importance of reliable glass solutions cannot be overstated. From protecting against break-ins to mitigating damage from natural disasters, investing in high-quality safety glass is a proactive step…





